I would like to show the danger of suspended virtual machines, with the tool called volatility there are several options you may extract from a vmem file can be found from the link below
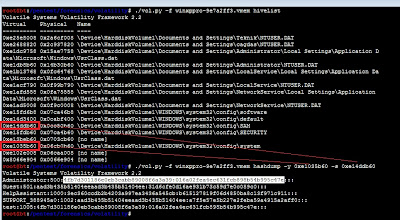
With in the example , we will find the local password for the related OS User
To use hashdump, pass the virtual address of the SYSTEM hive as -y and the virtual address of the SAM hive as -s, like this
Hashes can now be cracked using John the Ripper, rainbow tables, etc
In this example I have used cracker.offensive-security.com password appeared with in few minutes